Rogue Machine Event Monitor Reference Guide
Rogue Machine Event Monitor
Scans the network for new devices that may have connected to the network without permission.
Overview
The Rogue Machine Event Monitor searches your network for unrecognized systems.
Use Cases
- Detecting new systems that have connected to the network
Monitoring Options
This event monitor provides the following options:
Look for rogues in the local NetBIOS network
This option tells the event monitor to look in the local NetBIOS tables for unrecognized systems.
Look for rogues in the following IP ranges:
This option lets you specify IP address ranges where the even monitor will search for unrecognized systems.
Use ICMP pings to detect rogues
The event monitor can use multiple protocols to detect unrecognized systems. Use this option to tell it to use ICMP pings. ICMP pings are one of the best methods to detect rogue machines.
Use ARP requests to detect rogues
Use this option to tell the event monitor to use ARP requests to detect unrecognized systems. ARP requests only work on the local subnet.
Use HTTP requests to detect rogues
Use this option to tell the event monitor to use HTTP requests to detect unrecognized systems. HTTP requests will detect systems that are hosting web servers.
Use SNMP requests to detect rogues
Use this option to tell the event monitor to use SNMP requests to detect unrecognized systems. SNMP requests will detect networking equipment and other systems that support SNMP.
Alert with Warning/Error/Critical about changes in the list of found rogues since the last run
With this option enabled, the event monitor will remember the list of systems it found on the last run. If the current run detects any changes, the event monitor will alert you with the selected status level.
Don't alert about these devices
Use this option to exclude selected devices and tell the event monitor not to alert about them.
Authentication and Security
This event monitor does not require any authentication.
Protocols
Click on a protocol to learn more.
Data Points
This event monitor generates the following data points:
| Data Point | Description |
|---|---|
| Rogue Count | The number of rogues detected. |
Tutorial
To view the tutorial for this event monitor, click here.
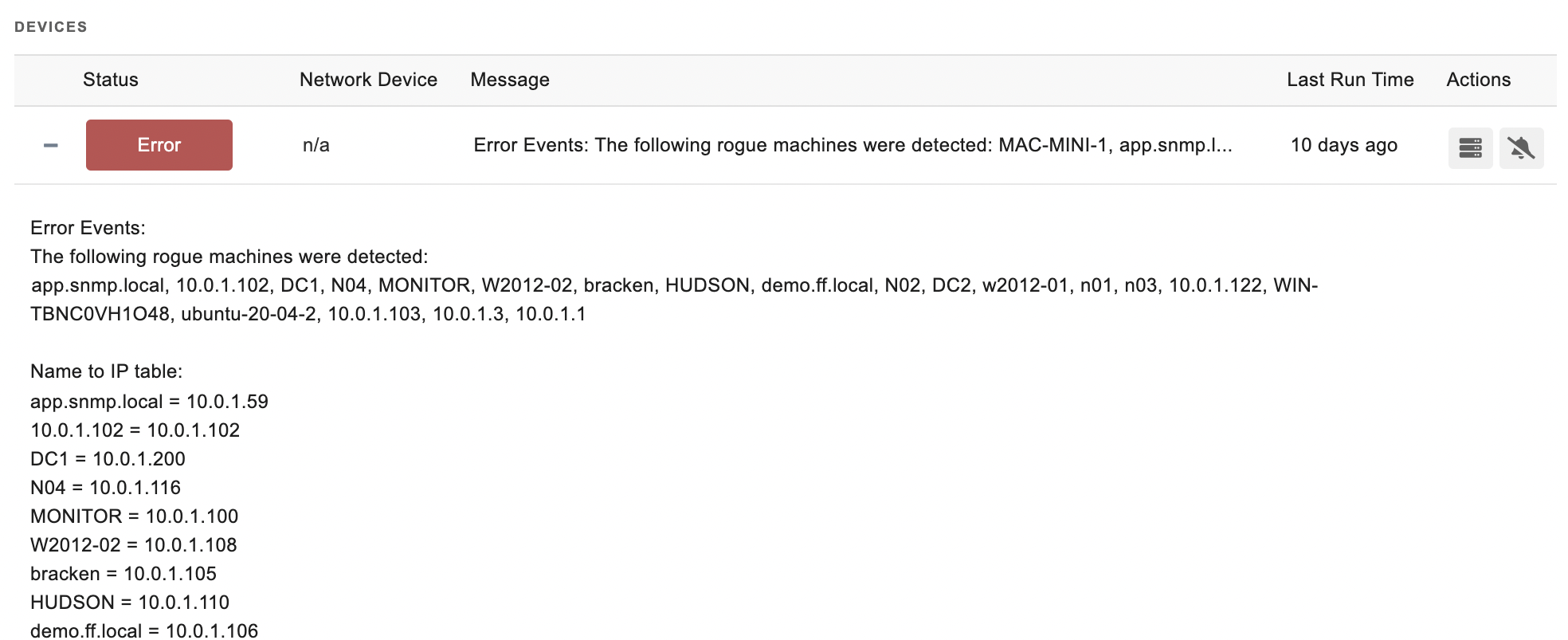
Sample Output
Comments
Add a comment