Microsoft Azure Certificate Event Monitor Reference Guide
Microsoft Azure Certificate Event Monitor
Alerts about certificate events and issues in your Microsoft Azure configuration.
Overview
The Microsoft Azure Certificate Event Monitor checks certificates in your Microsoft Azure key vaults and sends you alerts if the certificates are due to expire in a specified number of days.
Use Cases
- Receiving notification of certificates due to expire
- Keeping a list of all past and present certificates
Monitoring Options
This event monitor provides the following options:
Alert with [Info/Warning/Error/Critical] if Microsoft Azure cannot be contacted
Use this option to alert you if the event monitor is unable to connect to Microsoft Azure. Reasons for a failure to connect include invalid security tokens and loss of external network access.
Alert with [Info/Warning/Error/Critical] if there are new certificates since the last check
This option will send you an alert of your choice of urgency if the event monitor detects certificates that are new since the last time the event monitor ran.
Alert with [Info/Warning/Error/Critical] if there are expired certificates
When you enable this option, you'll receive an alert of your choosing if the event monitor detects one or more expired certificates.
Alert about certificates that will expire in less than a specified number of days
Here, you can specify how many days before a certificate expiry you'd like to receive each level of alert.
Don't alert about certificates that have already expired
Checking this box lets you filter out older alerts about certificates that have already expired.
Alert about certificates that will expire in more than a specified number of days
This option will send you alerts about certificates that expire later than expected so you can investigate why.
Don't alert about certificates that have been expired for more than [#] days
This sub-option will exclude certificates that have been expired for more than the number of days that you specify.
Don't alert about certificates that have already expired
This sub-option will exclude certificates that have expired in previous checks.
Alert about certificates that will expire in more than a specified number of days
This option will send you alerts about certificates that expire later than expected so you can investigate why.
Include a table of certificates [before all/after all] event text
This option lets you include a table of all certificates in the event text generated each time the event monitor runs.
Include all the certificates
This option lets you include all certificates in the table generated each time the event monitor runs.
Include valid certificates
This option lets you include all valid certificates in the table the event monitor generates.
Include expired certificates
This option allows you to receive a list of all expired certificates in the event text generated each time the event monitor runs.
Include certificates expiring in the next 30 days
This option, when selected, includes a list of any certificates due to expire in the 30 days following each event monitor run.
Only check the following key vaults
Enter one name per line of the key vaults you want to selectively check. Leave blank to check all key vaults.
Key vaults to ignore
Enter one name per line of the key vaults you want to ignore.
Certificates to ignore
Enter one name per line of the certificates you want the event monitor to ignore.
Authentication and Security
First, you'll need to create an app registration to add to your event monitor's authentication profile. Information on how to do this can be found in our "Creating an Azure Authentication Profile" article.
Your event monitor will also need Reader permissions at the subscription level. To configure this, go to your Azure portal and click Subscriptions > [Your Subscription] > Access Control (IAM) > Add Role Assignment, then search for "Reader". Then, add your app registration as a member and click "Review and Assign".
You'll also need to add the "Key Vault Reader" role assignment at the resource group level. To do this, search for "resource" and click on the "Resource Group" option that shows up. Choose the resource group and key vaults you want to use. It's good practice to specify each key vault you want to monitor in the event monitor, otherwise you'll have to do the aforementioned configuration for each key vault in your Azure environment. This event monitor also needs "Get" and "List" certificate permissions on each key vault.
Protocols
Data Points
This event monitor generates the following data points:
| Data Point | Description |
|---|---|
| Certificates | The current number of certificates. |
Tutorial
To view the tutorial for this event monitor, click here.
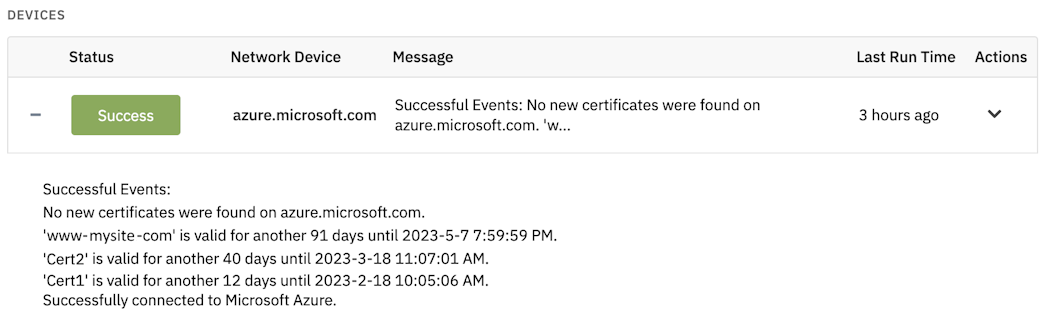
Sample Output
Comments
Add a comment