Technical Resources
Login Security: Users, Roles, and Groups
About Security Groups
FrameFlow has both login security users and groups. Users are collections of login settings/credentials for individuals. Groups are collections of security settings for multiple users. A user's permissions within FrameFlow are calculated by checking the security groups that include that user. These groups determine what parts of FrameFlow the user can view and modify.
Note: for more information on multi-site login and security rights and to learn what happens when a user is part of multiple security groups with different clearances, check out our other login security article.
Security Roles
Each group you create requires you to choose a security role. Roles are groups of permissions assigned to a security group. You can select from predefined roles like "Manager" or "View Only", or create custom security roles to assign to your users. For more information about how permissions work when a user is a part of more than one security group, read our advanced login security article.
Note: Another way to compartmentalize what different FrameFlow users get to see is with personal dashboards.
Ownership and Security
Security groups and roles both define how a user can and cannot interact with FrameFlow's various sections. However, you can also set a user as the owner of a device, event monitor, report, or dashboard by navigating to the desired item and clicking "Set Owners".
This means that even a user with low-level permissions can act as the owner of a device or other FrameFlow element from the list above. The owner of a device has manager permissions for that device only. You can assign multiple elements to the same user, allowing that user to manage a certain subsection of your FrameFlow configuration while keeping the user's permissions low in all other areas.
Groups as Members of Other Groups
You can even add security groups to other security groups.
Nesting security groups like this adds extra flexibility. Imagine your FrameFlow configuration has two security groups: Group A and Group B. Group A is a security group you've created that grants very basic permissions to all your users. Group B contains your most privileged users, your administrators.
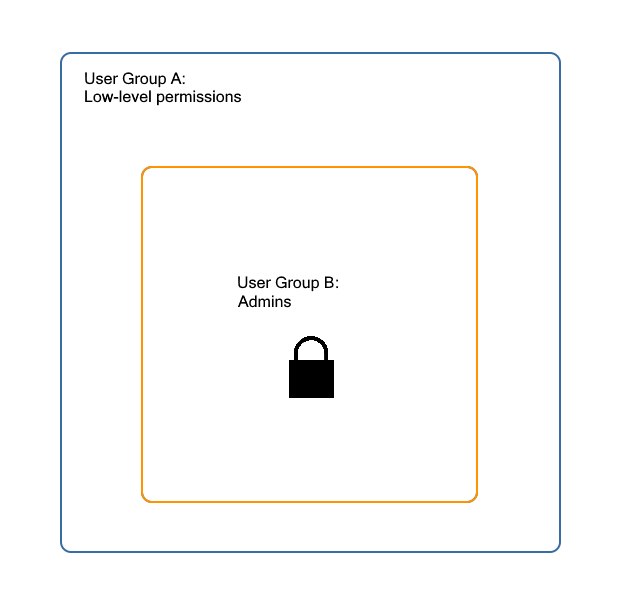
You could create these two groups independently of each other, giving Group A view rights only and giving Group B view rights plus administrator rights, for example. This will work for certain use cases, but if you ever wanted to change something about the lower-level permissions granted to both groups, you'd have to change it in two places.
By nesting the two groups like in the diagram above, Group A will have Group A permissions and Group B will have Group A + Group B permissions, meaning any edits made to Group A will affect permissions for both groups.
Mixing and Matching Security Group Login Types
When creating a security group, you must select a single login type from the list containing standard, Active Directory, or SAML. Before we added the option to add groups as members of other groups, there was no way to mix and match different login types within one security group. Now, by nesting security groups with different login types, you can give the same permissions but different login types to your users.
SAML Security Groups and Dynamic Membership
FrameFlow offers Single Sign On (SSO) through SAML as an optional login method. In FrameFlow v2024.5, we updated the way our SAML login types work. Now, when creating a new security group, there's an option called "Type" that lets you choose from standard, SSO, and AD login types. Just like before, when users log in with SSO, we create a FrameFlow account (of the type SAML) for them if we don't find a matching preexisting account. There’s also an option now to prevent these SAML accounts from being created if they aren’t mapped to one of our SAML groups. Group membership is now dynamic, meaning it lasts only for one login session.
Note: Members of both SAML and AD group types can also be members of standard groups.
Active Directory Security Groups and Dynamic Membership
Another login type FrameFlow offers authenticates users through Active Directory (AD). Since FrameFlow v2024.6, we've created a new Active Directory security group type that only AD users can be a member of, just like we explained above with SAML. There’s also the same option that SAML has to prevent AD accounts from being created if they aren’t mapped to one of our AD groups. AD group membership is also dynamic and only lasts for one login session.
Those groups work by allowing you to specify an AD group from Windows to map the login to. When a user logs in, it will create a new FrameFlow account (of type AD) for them if one doesn't exist already. Like SAML, when they log in, we check each of our AD groups to see if they match what Windows gave us. They get membership to those groups for that login session.